SAML authentication (SCIM optional)
Available for Express and Enterprise Editions only.
Security Assertion Markup Language (SAML) lets Prophecy delegate user authentication to your identity provider (IdP). System for Cross-domain Identity Management (SCIM) optionally automates provisioning and deprovisioning of users and teams from your IdP into Prophecy.
This page describes how to set up SAML and SCIM, which requires configuration in both Prophecy and your preferred IdP.
Prerequisites
Review the following prerequisites.
- To access SSO settings, you must be a cluster admin for your deployment.
- SAML is available for Express and Enterprise Editions.
- SCIM is only available for the Enterprise Edition. To enable SCIM in your environment, update the
configin your Prophecy deployment.
Supported identity providers
Prophecy supports the following identity providers (IdP):
- Okta
- Azure Active Directory (Microsoft Entra ID)
- Others (custom)
Prophecy-specific steps
Set up SAML
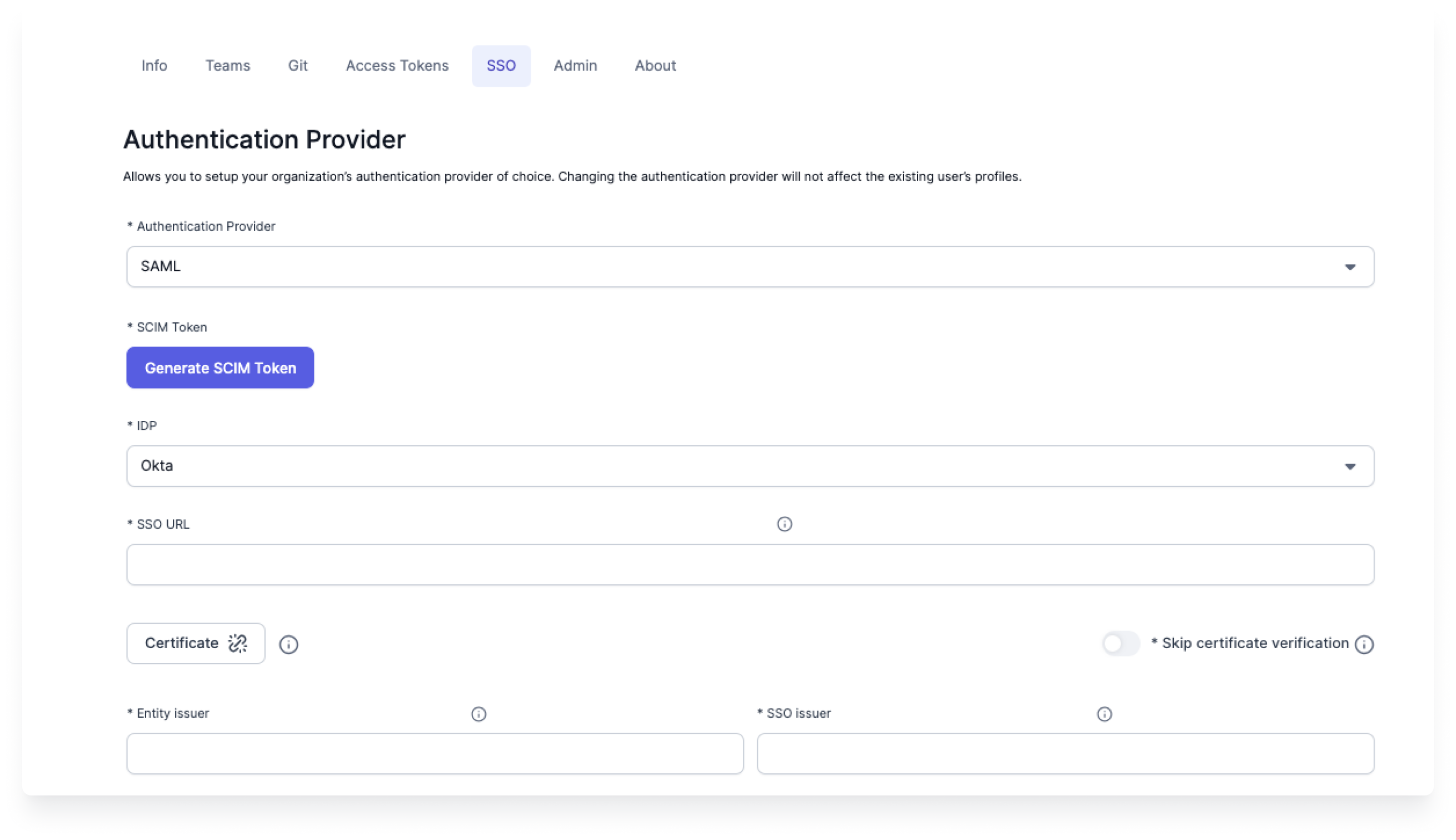
To set up SAML authentication in Prophecy:
-
Log in to Prophecy as a cluster admin user.
-
Navigate to the SSO tab of the Prophecy Settings page.
-
Under Authentication Provider, select SAML.
-
Under IdP, select the appropriate identity provider.
-
Fill out the remaining parameters:
Parameter Description Generate SCIM Token If SCIM is enabled in your environment, click to create/rotate the SCIM bearer token used by your IdP/SCIM client to provision users and groups. SSO URL The Identity Provider Single Sign-On endpoint. Paste the SSO URL (Location) from your IdP metadata. Prophecy redirects users here to authenticate. Certificate The IdP SAML signing certificate. Prophecy uses this to verify SAML response signatures. Skip certificate verification Disable TLS certificate/host verification when calling the IdP SSO endpoint. Entity issuer The entity issuer you configured in the IdP. Usually, this is the label for your SAML configuration. SSO issuer The SSO issuer. For Azure AD this is the Azure AD Identifier; for Okta, it is the issuer link in the XML. -
Click Save at the bottom of the page to save your changes.
Set up SCIM
SCIM allows Prophecy to automatically provision and deprovision users and teams based on your IdP configuration. To set up SCIM in Prophecy:
- Ensure that SCIM is enabled in your Prophecy environment.
- Complete the SAML configuration described above.
- Click Generate SCIM Token and copy the value of the token. You will use this in your IdP settings later.
After completing these steps, you'll create users and groups in your IdP directly. See Group-to-team mapping to learn about group naming conventions.
IdP-specific steps
The following sections describe the fields you must configure in your IdP settings to complete the SAML/SCIM setup.
Azure Active Directory
Configure SAML for Azure Active Directory (Microsoft Entra ID) and enable SCIM provisioning
- Log into AzureAD as an administrator and create a new Enterprise Application like
ProphecyAzureADApp. - In the home page search bar, search for Enterprise Applications.
- Click New Application > Create your own application.
- Give name for the application like
ProphecyAzureADApp. - Choose the radio button Integrate any other application you don't find in the gallery (Non-gallery).
- Click Create.
- In Manage section on the left, click Single sign-on.
- Choose SAML as the Single sign-on method.
Now the form for Set up Single Sign-On with SAML will open. You'll have to fill out different sections of the form.
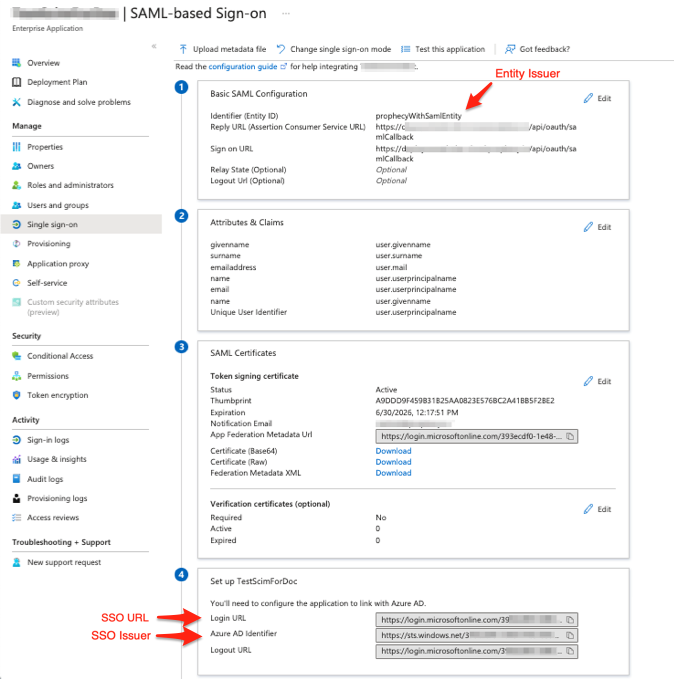
Basic SAML Configuration
- Provide an Identifier (Entity ID) which is a unique ID to identify this application to Microsoft Entra ID. This will be added to the Entity issuer field in Prophecy.
- In the same section, configure Reply URL and Sign on URL as:
https://your-prophecy-ide-url.domain/api/oauth/samlCallback - Click Save.
Attributes & Claims
- Click Edit button and then Add new claim.
- Give Name as
emailand Source Attribute asuser.userprincipalname, and click Save. - Add one more claim by clicking on Add new claim.
- Give Name as
nameand Source Attribute asuser.givenname, and click Save.
SAML certificates
In the SAML certificates section, download Certificate (Base64) file to be used while configuring SSO in Prophecy UI.
Set up ProphecyAzureADApp
In the Set up ProphecyAzureADApp section, copy Login URL and Azure AD Identifier to be used while configuring SSO in Prophecy UI.
Configure provisioning
To set up SCIM in Azure:
-
Open the Enterprise Application you just configured.
-
From the left menu of the application, click Manage > Provisioning.
-
From the left menu of the provisioning page, click Manage > Connectivity.
- Under Select authentication method, select Bearer authentication.
- For the Tenant URL field, use the value
https://<your-deployment-name>.prophecy.io/proscim - For Secret token, use the Prophecy-generated token that you copied in the Set up SCIM steps.
- Click Test connection. Once the test succeeds, you can save the connection.
-
From the left menu of the same provisioning page, navigate to Manage > Provisioning.
- Set the Provisioning Mode to Automatic.
- Ensure that the Provisioning Status toggle is set to On.
-
From the left menu of the same provisioning page, navigate to Manage > Users and groups.
- Create groups using Prophecy's naming conventions.
- Assign users to those groups.
These users and teams should automatically appear in Prophecy.
Okta
Configure SAML for Okta and enable SCIM provisioning
- Log in to Okta as an administrator.
- On the homepage, navigate to Applications > Applications.
- Click Create App Integration.
- Select SAML 2.0 and click Next.
- Enter App Name as Prophecy SAML App and click Next.
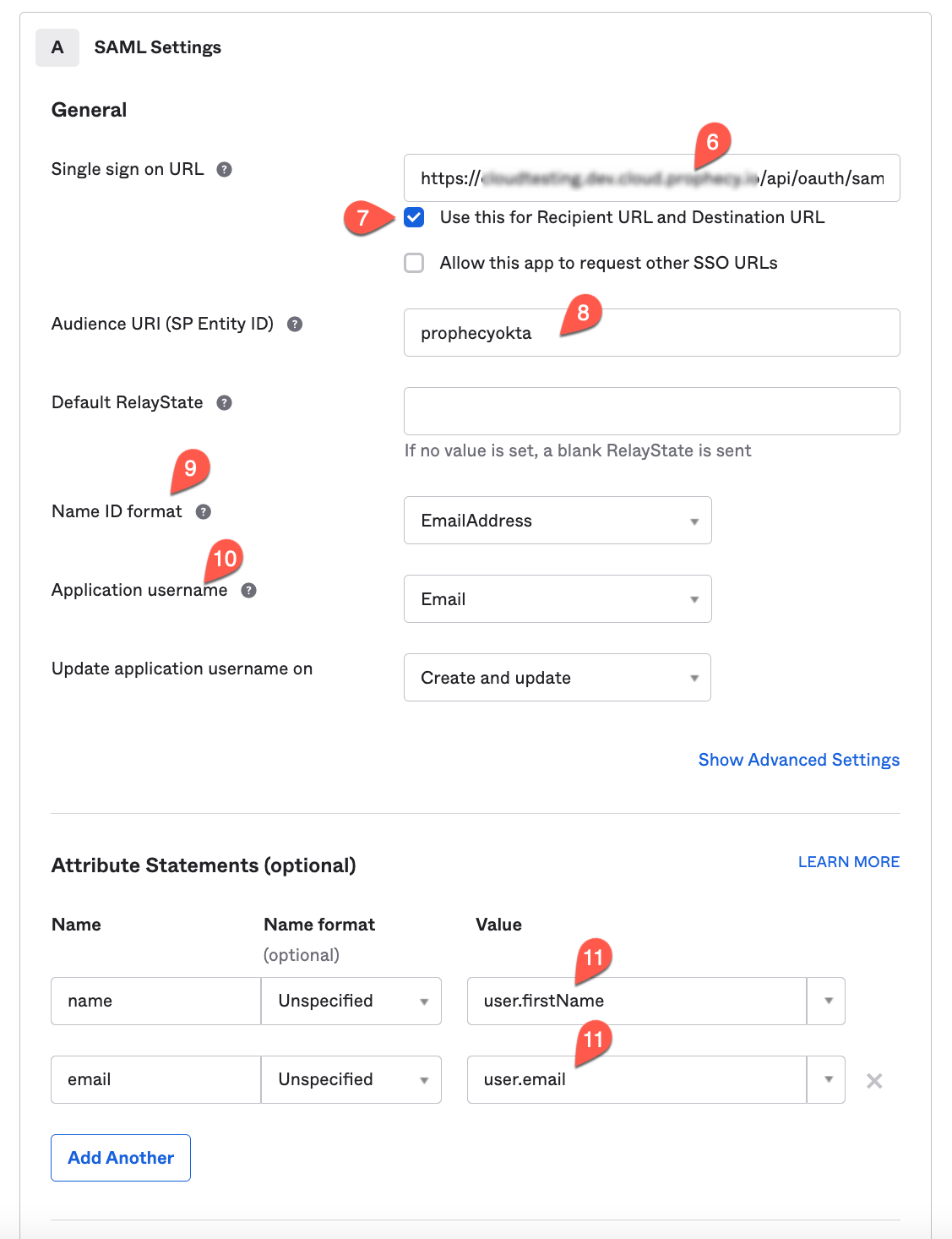
- For Single Sign-On URL, specify
https://your-prophecy-ide-url.domain/api/oauth/samlCallback. - Select Use this for both Recipient URL and Destination URL.
- In Audience URI (SP Entity ID), provide a name to serve as the entity issuer ID (e.g., prophecyokta).
- Set Name ID format to EmailAddress from the dropdown.
- For Application Username, select Email.
- Under Attribute Statements, add two attributes name and email.
- Click Next.
- Choose I’m an Okta customer adding an internal app.
- Click Finish. The Prophecy SAML App is now displayed.
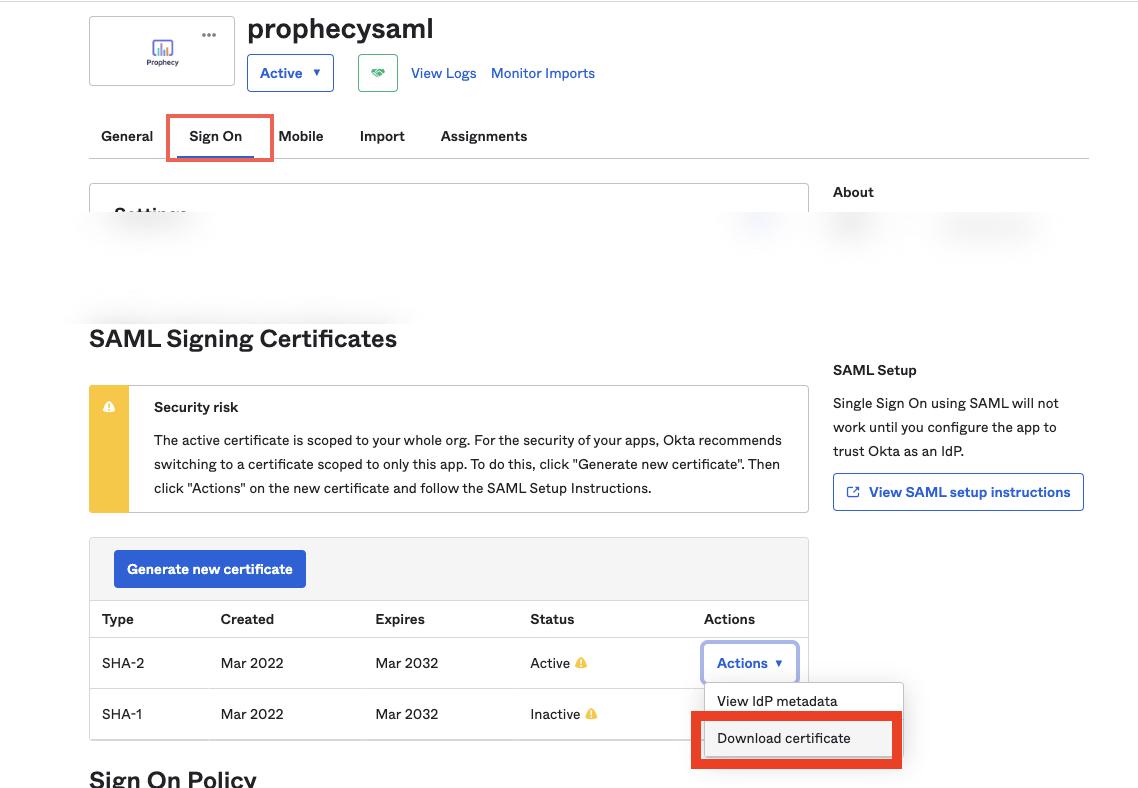
Download SAML Signing Certificate
- Navigate to the Sign On tab of Prophecy SAML App in Okta.
- Locate the SAML Signing Certificates section.
- Click the download button, as shown in the example below, to download the certificate:
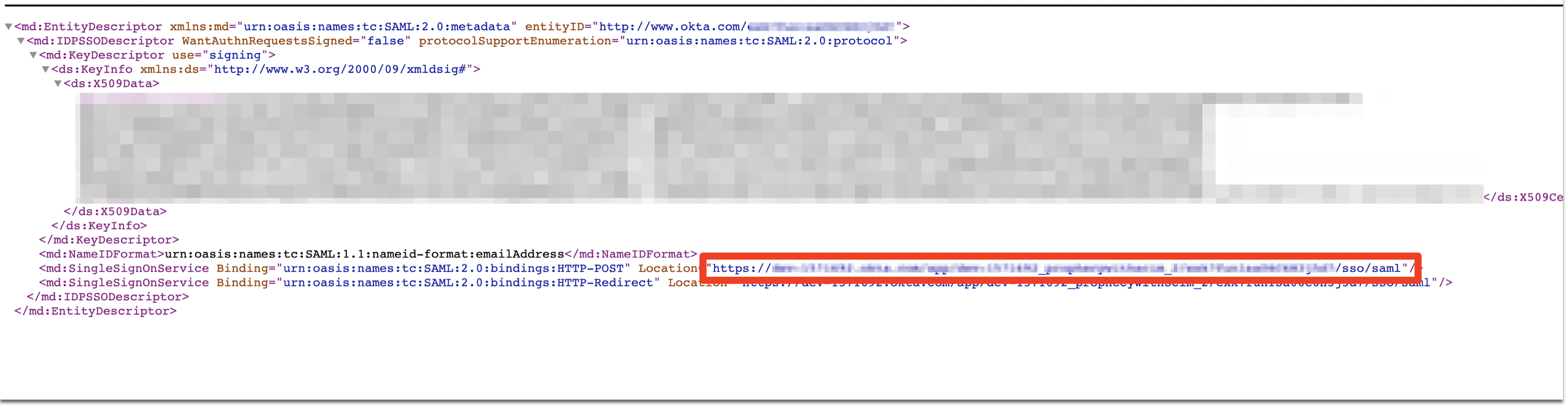
SSO URL
- In the same Sign On tab under SAML Signing Certificates, click View IdP metadata.
- This action opens an XML file in a new browser tab.
- Copy the red-highlighted text in the Location section of the XML file and use it as the SSO URL in Prophecy IDE.
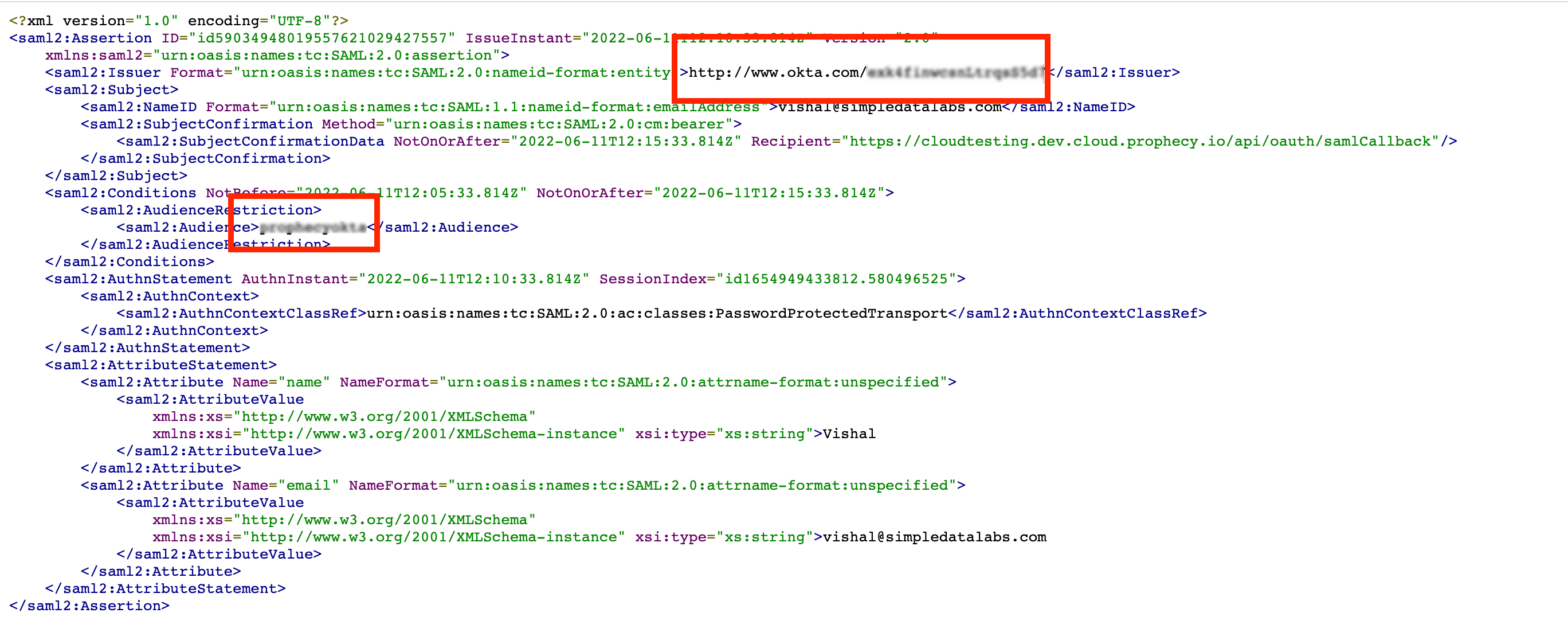
Entity and SSO Issuer
- Go to the General tab, then navigate to the SAML Settings section and click Edit.
- Click Next to reach the Configure SAML section.
- Scroll to the bottom and click the Preview the SAML assertion button.
- This opens a new browser tab.
- Copy the highlighted information from the preview and use it as the Entity Issuer and SSO Issuer in Prophecy IDE.
Enable SCIM provisioning
To set up SCIM in Okta:
- Open in Prophecy application in Okta.
- In the General settings, select the Enable SCIM provisioning checkbox.
Once SCIM is enabled, two new tabs should appear in the application settings: Provisioning and Push Groups.
-
Navigate to the Provisioning tab.
-
In the To App subtab, enable the following:
- Create Users
- Update User Attributes
- Deactivate Users
This allows Okta to perform the enabled actions in Prophecy.
-
In the Integration subtab:
- Set the SCIM version to
2.0. - For the SCIM connector base URL, use the value
https://<your-deployment-name>.prophecy.io/proscim - For the Unique identifier field for users, type
userName. This is an Okta-specific value. - For Supported provisioning actions, ensure that Push New Users, Push Profile Updates, and Push Groups checkboxes are enabled.
- Set the Authentication Mode to HTTP Header.
- Under HTTP Header, set the Bearer token to the Prophecy-generated token that you copied in the Set up SCIM steps.
- Click Test Connector Configuration.
- When successful, click Save.
- Set the SCIM version to
Now that you have set up the connection, you need to create and activate your group assignments.
- Open the Assignments tab.
- Create users and assign them to groups using Prophecy's naming conventions.
- Navigate to the Push Groups tab.
- Follow the steps in Enable Group Push in the Okta documentation to activate group provisioning in Prophecy.
Once you have pushed groups, the corresponding users and teams should appear in Prophecy. When groups are "active" in Okta, any changes to these groups should automatically sync with Prophecy.